This Device Can Break Into Any iPhone

Smartphones have become our primary devices very quickly. Our documents, pictures, music, everything resides in our palm thanks to smartphones. Also, over the years, smartphones have come under scrutiny for their lacklustre security. A few months ago, OnePlus 5 was found to be vulnerable to hacking. While that was software based, a new device claims to be able to break into any iPhone.
GrayKey
A new device called GrayKey looks, ironically, like an Apple TV and can bypass any iPhone’s security code. The device is made by Grayshift, an Atlanta, US-based company and comes to light after the recent debate around company ethics and smartphone security. A couple of years ago, FBI asked Apple to give it access to the iPhones of San Bernardino shooters. Apple declined and FBI discovered that there are third-party services that can break into iPhones. While FBI was able to bypass those iPhones, it is surprising that Apple has not yet closed that backdoor access.
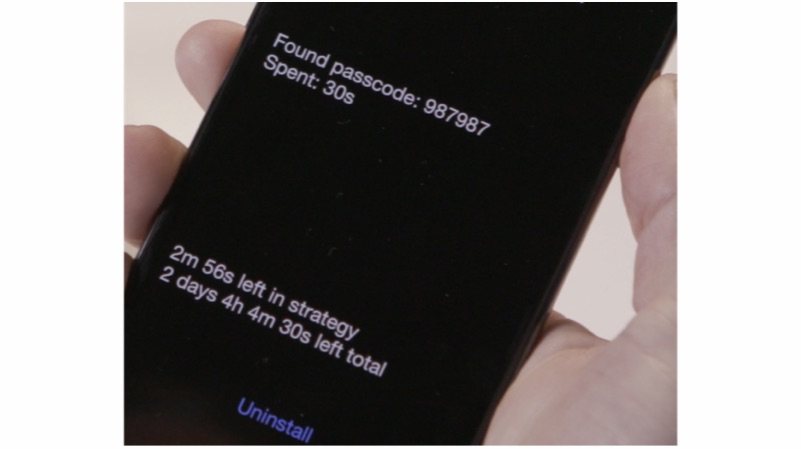
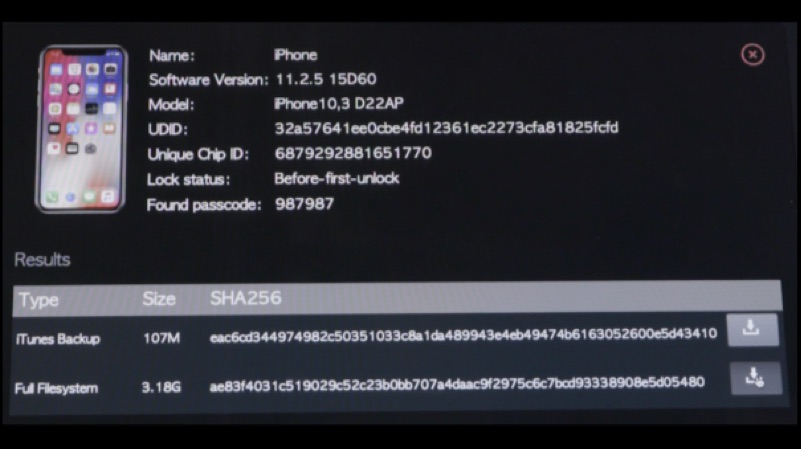
GrayKey has two lightning cables attached to it. The process of hacking into an iPhone starts with the iPhone being connected to the device for two minutes. After two minutes, the iPhone is disconnected and it shows a black screen. The black screen then displays the passcode and other information. However, it is worth noting that this process depends on how complex the passcode. It can even take up to two days to crack the code.
Grayshift claims that even disabled phones can be cracked. Once the iPhone is unencrypted, all the data is downloaded to the GrayKey device. What is even more mindboggling is the price of this device. The GrayKey is available in two variants, the US$ 15000 (Rs 975,675 approx.) model needs an internet connection, and is geofenced to work on a single network. The other variant costs a whopping US$ 30,000 (Rs 1,951,350 approx.) which doesn’t need an internet connection and can bypass devices as the owner wants.
It is worth noting that these devices will be nullified if and when Apple comes up with a fix for this vulnerability.